Clone Systems - Business Security Intelligence
Properly Secure Your Enterprise Network

Clone Systems is a global network security provider established in 1998. Since our company’s inception, we have distinguished ourselves by delivering innovative security solutions and services, around-the-clock customer support, and service guarantees, which are among the most comprehensive in our industry.
Managed Penetration Testing:
Perform real world attack simulations on your infrastructure to identify existing vulnerabilities and obtain recommendations on how to improve your overall security
Obtain support, education, and guidance from certified security engineers on how to improve your network
- Managed by our certified security engineers who have extensive experience with assessing vulnerabilities for both security and compliance
- Detailed vulnerability report including high, medium, and low vulnerabilities found and exploited with remediation guidance and recommendations
Improve your overall security posture and your policies and procedures by understanding the vulnerabilities within your network and how to remediate them
- Identify and exploit vulnerabilities by simulating real-world attacks to assess the security posture of your network
- Robust solution using the latest technology comprised of a combination of best of breed open source, and proprietary tools
- 4 days of comprehensive testing with a combination of white hat and black hat techniques with and without passwords to assess your network
- Perform internal and external penetration testing customized to meet your business requirements
- Social engineering options available that imitate techniques used by hackers to target your employees to obtain your company’s private information
- Ample time included for remediation followed by a rescan of your environment to assess the status of vulnerabilities
Meet and exceed audit, regulatory and compliance requirements validated by Clone Systems security expertise
- Certified pass report after assessing that there are no high or medium vulnerabilities in your environment
- Includes 1 year access to our OnDemand web-based scanning portal to allow your team to perform ongoing assessments of your security posture
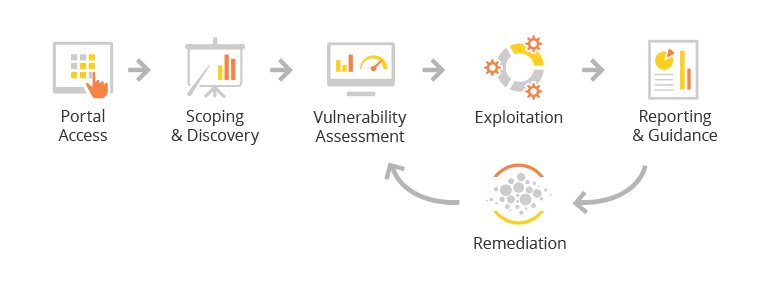
How Managed Penetration Testing Works
Our team of certified security engineers will work closely with you to understand your business requirements, identify the infrastructure and applications that will be in scope for the penetration test, and to schedule the 4 days of comprehensive testing. They will then simulate real-world attacks against the in-scope assets using best of breed open source and proprietary tools with the latest threat intelligence. A combination of white hat and black hat techniques will be leveraged to validate your internal and external security controls and to discover any weaknesses that can be used to compromise and gain unauthorized access to your environment. Any identified risks and vulnerabilities will be documented and our security engineers will review the findings with your team and provide guidance on how to remediate the vulnerabilities and improve your security posture. Ample time will be provided to your team to address and resolve the findings after which we will conduct another rescan of your environment. Upon confirming that the identified security risks and vulnerabilities have been addressed we will provide a certified pass report that can be used to meet your audit, regulatory and compliance requirements.
Ondemand Penetration Testing
Perform real world attack simulations on your infrastructure to identify existing vulnerabilities and obtain recommendations on how to improve your overall security
Proactively assess your network for vulnerabilities and identify corrective actions
- OnDemand web-based portal to conduct self-managed penetration testing
- 7-day access for unlimited scanning of up to 255 IPs on your network to assess vulnerabilities for security and compliance*
- Perform internal and external penetration testing customized to meet your business requirements
Improve your overall security posture and your policies and procedures by understanding the vulnerabilities within your network and how to remediate them
- Identify and exploit vulnerabilities by simulating real-world attacks to assess the security posture of your network
- Detailed vulnerability report including high, medium, and low vulnerabilities found and exploited with remediation guidance
Meets compliance requirements validated by Clone Systems security expertise
- Certified pass report after assessing that there are no high or medium vulnerabilities in your environment
How Ondemand Penetration Testing Works
Your team can proactively test your internal and external security controls and assess your infrastructure for vulnerabilities and weaknesses that can be used to compromise and gain unauthorized access to your environment by conducting a self-managed penetration test using a comprehensive security scanning solution with the latest threat intelligence. A series of real world attack simulations will be performed against the assets that you configure within the solution and any identified risks or vulnerabilities will be highlighted in a detailed vulnerability report with remediation guidance. Your team can then work to resolve the findings and then rescan your infrastructure to confirm that any identified security risks and vulnerabilities have been addressed. Once the assets are secured from all known high and medium vulnerabilities a certified pass report can be accessed and used to meet your audit, regulatory and compliance requirements.
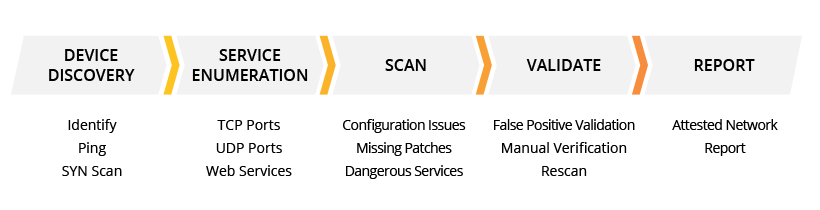
Our battery of security management benchmarks are rigorous and uncompromising. Some of the high level analysis and performance evaluation stages that are conducted by the OnDemand Penetration testing include the following:
- Reconnaissance encompasses passive and active reconnaissance tactics to identify and evaluate your network topology, active hosts, IP addresses, installed operating systems, open network ports, and all installed security devices.
- Analysis entails performing application mapping, network scanning/fuzzing, and vulnerability analysis. It effectively identifies all applications running behind open network ports and their degree of potential vulnerability The Analysis stage typically involves running SQL Injection, Code Injection, Code Execution, Directory Traversal, and Cross Site Scripting against the web applications to expose any security anomalies.
- Penetration employs the data derived from the Analysis stage to exploit the determined weak points of your network to attempt to gain access. Typically, the Penetration phase focuses primarily on vulnerabilities revealed for network services and externally facing web applications.
- Information. This phase generates alerts once a vulnerability has been successfully exploited. A system restore is immediately performed to return the network to its previous state prior to the intrusion. A detailed report is generated on all areas of your enterprise for assessing how and why the intrusion was successful.
- Finally, the Documentation phase reflects all testing results, all intrusions, the areas of the system that were compromised during an intrusion, intrusion-resistance recommendations, and qualitative analysis reports of each security mechanism employed on your network.
Payment Card Industry (Pci) Compliance Scanning
Comply with the Payment Card Industry Data Security Standard (PCI DSS) and safeguard your customer’s data
Leverage a robust PCI data security scanning solution from an Approved Scanning Vendor (ASV) that meets all the PCI Security Standards Council requirements
- Easy to use self-managed web-based scanning portal which enables you to maintain PCI compliance by scheduling and running scans every 90 days or as often as you want
- Analyze your solutions that store, process, or transmit cardholder data for threats and vulnerabilities that could expose sensitive data
Minimize the risk of compromise for cardholder data and the potential impact on your organization
- Detailed remediation steps for protecting against identified vulnerabilities detected during your PCI security scan
- Unlimited re-scans on your network to assess steps taken to fix vulnerabilities
- Threat intelligence and signature updates consistently updated from multiple security sources to protect against emerging threats and vulnerabilities
Fulfill PCI compliance reporting requirements for the acquiring banks, card brands or other requesting entities you do business with
- Executive, Detailed and Attestation PCI reports with ASV certification number to address your assessment and compliance reporting requirements
- Online Self-Assessment Questionnaire (SAQ) for all the different SAQ types to assist you with reporting the results of your PCI DSS self-assessment
How PCI Compliance Scanning Works
Payment Card Industry (PCI) compliance scans are conducted through a self-managed web-based PCI Compliance Scanning portal which is consistently updated with the latest threat intelligence and certified annually to meet all the PCI Security Standards Council requirements. Using a simple interface or intuitive wizard you configure, schedule and run scans for the hosts that store, process or transmit cardholder data. If vulnerabilities are identified you are presented with details about the vulnerabilities and remediation steps that can be used to address them. Your team can then work to resolve the findings and then rescan the hosts to confirm that any identified vulnerabilities have been addressed. Once your hosts that process credit card information are secured from all known high and medium vulnerabilities the Executive, Detailed and Attestation PCI compliance reports will be certified with a passing status and can be delivered to your acquiring banks, card brands or other requesting entities you do business with. Additionally, the portal provides a Self-Assessment Questionnaire (SAQ) wizard that can be used to help you identify the SAQ type that aligns with your business requirements so you can complete an online version of the SAQ and report the results of your PCI Data Security Standards (DSS) self-assessment.
Vulnerability Assessment
Assess the security and integrity of your infrastructure to identify vulnerabilities and obtain recommendations on how to improve your overall security posture
Proactively assess your network to identify and prioritize your network security threats
- Easy to use self-managed web-based scanning portal which enables you to schedule and run scans as needed
- Perform internal and/or external vulnerability testing to obtain a deeper understanding of your overall security posture
Minimize the risk of a security breach by providing insights and guidance to properly secure your network
- Detailed remediation steps for protecting against identified vulnerabilities detected during your vulnerability assessment
- Unlimited re-scans on your network to assess steps taken to fix vulnerabilities
- Threat intelligence and signature updates consistently updated from multiple security sources to protect against emerging threats and vulnerabilities
Obtain executive level and detailed technical reporting for the vulnerabilities that exist in your infrastructure
- Pass report after assessing there are no existing high or medium level vulnerabilities in your environment
How Vulnerability Assessment Works
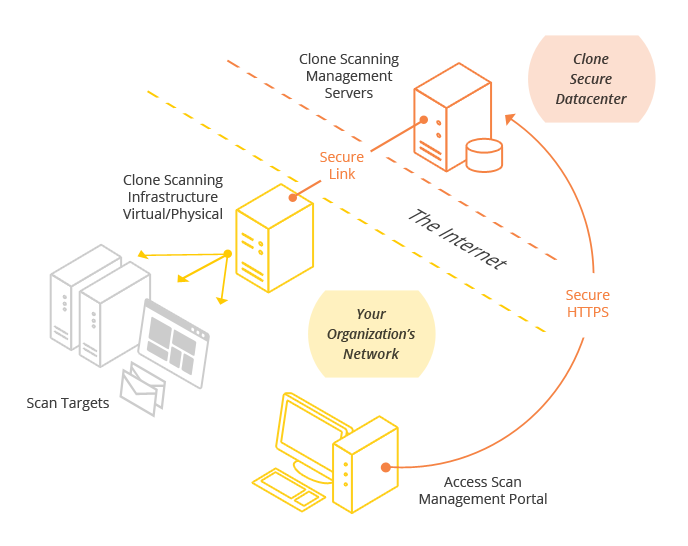
External Vulnerability Scanning
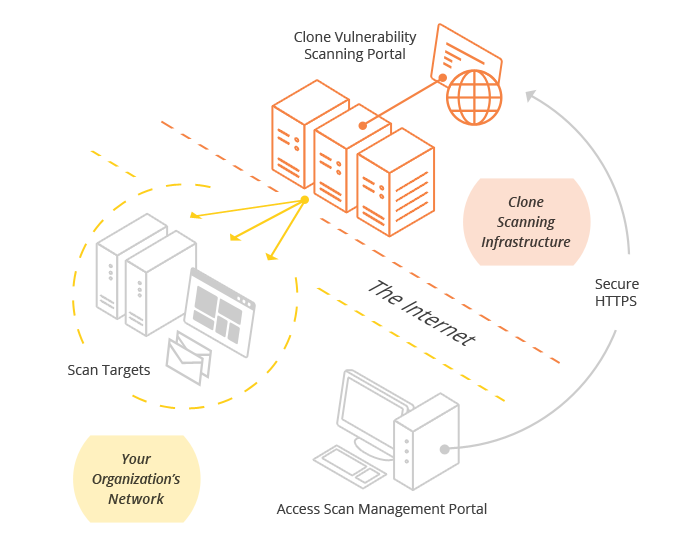
External vulnerability scans are scheduled through the Clone Systems Vulnerability Assessment portal. When the scans are executed our scanning infrastructure assesses the hosts identified in the scan criteria against our threat intelligence and signatures in order to identify any existing threats, vulnerabilities or weaknesses. The results are then recorded in our solution and available via the Clone Systems Vulnerability Assessment portal so that you can review remediation steps and take any necessary actions. Upon remediating you can rescan the hosts to determine the status of your security posture.
Internal Vulnerability Scanning
Internal vulnerability scans require you to configure a Clone Systems scanning server within your network. The scanning server can either be a physical server or a virtual server and we support the majority of virtual environments (VMware, VirtualBox, Microsoft Hyper-V, and Citrix XEN to name a few). Upon configuring the internal scanning server and confirming secure connectivity back to the Clone Systems SOC you can schedule the vulnerability scan through the Clone Systems Vulnerability Assessment portal. When the scans are executed our solution communicates directly with the scanning server within your network to assesses the hosts identified in the scan criteria against our threat intelligence and signatures in order to identify any existing threats, vulnerabilities or weaknesses. The results are then recorded in our solution and available via the Clone Systems Vulnerability Assessment portal so that you can review remediation steps and take any necessary actions. Upon remediating you can rescan the hosts to determine the status of your security posture.
Intrusion Prevention Services (IPS)
Monitor your network in real-time to detect and prevent threats
Protects your business in real-time against global emerging threats and vulnerabilities
- Threat intelligence and signature updates consistently updated from multiple security sources that details how to detect and protect against emerging threats and vulnerabilities
- 24/7 Monitoring and alerting that leverages threat intelligence to block threats and vulnerabilities automatically
- Security Operation Center monitoring your security environment, tuning the IPS to distinguish critical threats from false positives, and escalating as needed 24/7/365
Provides additional security resources via managed solutions that free your team to focus on driving core business value
- Vendor agnostic expertise enabling our solutions and skilled security engineers to work with any existing security infrastructure on your network
- Clone Guard® Network Security delivered as a fixed cost service without requiring any capital expenditures from your budget
- Software updates and patches maintained by our security engineers to address security infrastructure bugs and vulnerabilities
Addresses your business and compliance needs with executive level and detailed reports and dashboards enabling you to visually investigate the threats and vulnerabilities targeting your business
- Actionable reporting tailored to your business needs, compliance standards, and investigative requirements
- Customizable dashboards providing a visual representation of threats and vulnerabilities allowing you to filter detailed security event information
*Option for Intrusion Detection Services (IDS) which allow you to monitor and detect threats
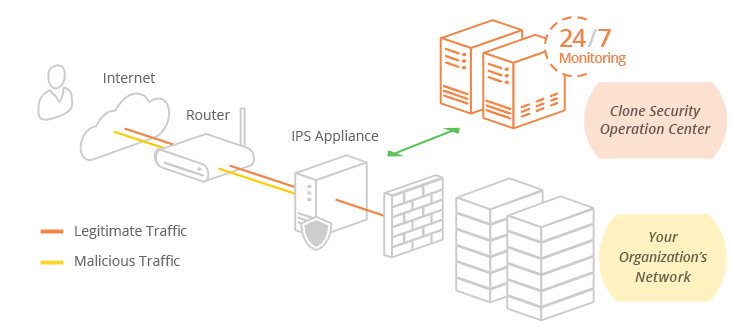
How Intrusion Prevention Services (Ips) And Intrusion Detection Services (IDS) Works
Intrusion Prevention Services (IPS)
The IPS appliance is configured according to your network throughput and interface requirements and is typically installed in-line (also known as in-band) between your edge router and your primary firewall. The IPS runs in protection/prevention mode and inspects all network traffic routed to your infrastructure in real time against consistently updated threat intelligence and signature updates. Upon finding malicious traffic such as a denial of service, brute force attack, worms, software and network exploits to name a few, the appliance immediately drops the packets preventing the attack from reaching its intended target. The Clone Systems Security Operations Center (SOC) consistently monitors this activity and the appliance 24/7 to tune the IPS to distinguish critical threats from false positives and to escalate threats as needed. Note that it is also recommended to have an IPS appliance configured internally within your network to analyze traffic that was originally encrypted with Transport Layer Security (TLS) / Secure Sockets Layer (SSL) / Internet Protocol Security (IPsec) as this traffic cannot be inspected until it is unencrypted.
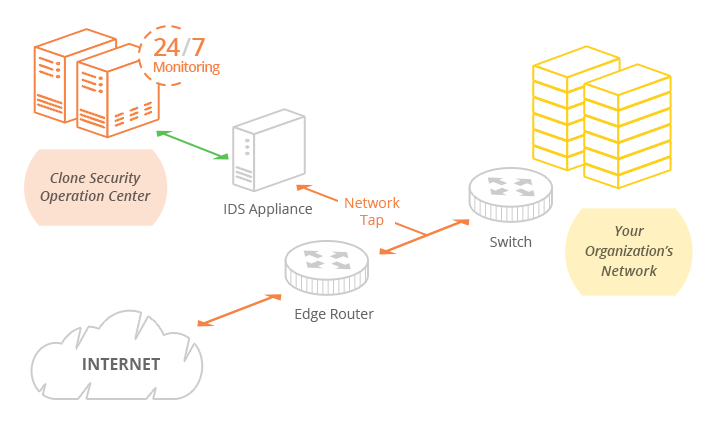
Intrusion Detection Services (IDS)
VoIP Intrusion Prevention Services (VoIP IPS)
Monitor your voice infrastructure in real-time to protect against attacks aimed at causing service disruptions and to detect and prevent threats that exploit VoIP specific vulnerabilities
Preserves the quality of service and protects your VoIP network in real-time against global emerging threats and vulnerabilities
- VoIP specific Threat intelligence and signature updates consistently updated from multiple security sources that details how to detect and protect against emerging threats and vulnerabilities targeting your voice network
- Preemptive protection against common categories of VoIP attack techniques that include denial of service (DoS), unauthorized call monitoring, loss of control, service theft and call routing manipulation
- 24/7 Monitoring and alerting to block threats and vulnerabilities automatically in order to maintain the security and availability of your VoIP network
- Security Operation Center monitoring your VoIP infrastructure, tuning the VoIP IPS to distinguish critical threats from false positives, and escalating as needed 24/7/365
Addresses your business and compliance needs with executive level and detailed reports and dashboards enabling you to visually investigate the VoIP threats and vulnerabilities targeting your business
- Actionable reporting tailored to your business needs, compliance standards, and investigative requirements
- Customizable dashboards providing a visual representation of VoIP threats and vulnerabilities allowing you to filter detailed security event information
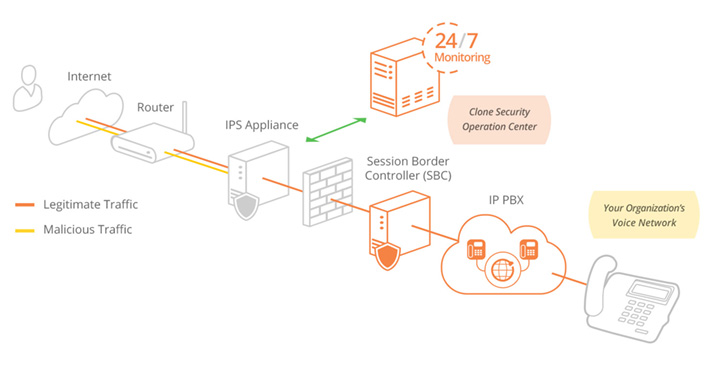
How VoIP Intrusion Prevention Services (VoIP IPS) Works
Voice over Internet Protocol Intrusion Prevention Services (VoIP IPS)
The VoIP IPS appliance is configured according to your network throughput and interface requirements and is typically installed in-line (also known as in-band) in front of your VoIP gateway, network and phone infrastructure. The IPS runs in protection/prevention mode and inspects all network traffic routed to your voice network in real time against consistently updated threat intelligence and signature updates. Upon discovering malicious traffic that attempts to disrupt or manipulate the voice network via attack techniques such as a denial of service (DoS), eavesdropping, call hijacking, toll fraud, worms, viruses, buffer overflows, software and network exploits targeting VoIP devices to name a few, the appliance immediately drops the packets preventing the attack from reaching its intended target. The Clone Systems Security Operations Center (SOC) consistently monitors this activity and the appliance 24/7 to tune the VoIP IPS to distinguish critical threats from false positives and to escalate threats as needed.
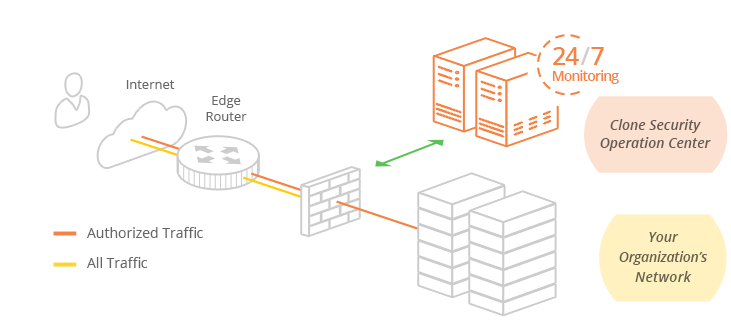
Managed Firewall
Infuse best practices and optimize firewall configurations
Enhances the protection of your business network and provides supplemental support and security expertise
- Setup, configure, tune, and optimize security infrastructure incorporating industry best practices and rule sets to ensure the security of your network
- 24/7 Monitoring, alerting, and reporting of your security infrastructure
- Security Operation Center monitoring and tuning your security infrastructure and escalating as needed 24/7/365
Delivers proper network security for your unique business requirements through collaboration with certified security engineers with extensive global and industry specific experience and expertise
- Vendor agnostic expertise with best of breed security devices enabling our certified security engineers to patch and maintain your infrastructure firmware and help troubleshoot issues
- Secure communications with your external workforce, partners and vendors via Virtual Private Networks (VPNs) to protect the integrity of transmitted data
- Specialized recommendations for network infrastructure and architecture design that optimizes the security and enhances the availability of your network
How Managed Firewall Works
Our team of certified security engineers will work closely with you to review your current network infrastructure, architecture, security goals and objectives so that we can validate your firewall configurations and rule sets to ensure they are optimized to achieve your business requirements. We partner with your existing team to continually manage your firewall infrastructure, help troubleshoot and resolve issues, infuse best practices and tune your security infrastructure while seamlessly integrating with your change management process to implement approved requests, security patches and firmware updates required to properly secure your business. Your protection is further enhanced by our Security Operation Center (SOC) which provides 24/7 monitoring, alerting and reporting for your security infrastructure and escalates issues as needed.
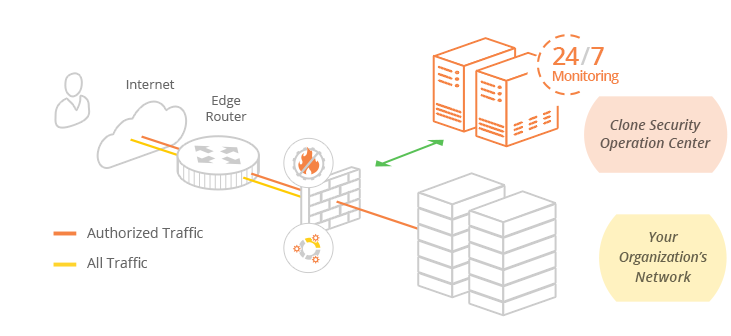
Nextgen Firewall
Infuse best practices and optimize NextGen firewall configurations
Enhances the protection of your business network and provides supplemental support and security expertise
- Setup, configure, tune, and optimize security infrastructure (including firewalls, NextGen firewalls/UTMs, endpoints/BYOD, and secure VPNs) incorporating industry best practices and rule sets to ensure the security of your network
- 24/7 Monitoring, alerting, and reporting of your security infrastructure
- Security Operation Center monitoring and tuning your security infrastructure and escalating as needed 24/7/365
Delivers proper network security for your unique business requirements through collaboration with certified security engineers with extensive global and industry specific experience and expertise
- Vendor agnostic expertise with best of breed security devices enabling our certified security engineers to patch and maintain your infrastructure firmware and help troubleshoot issues
- Secure communications with your external workforce, partners and vendors via Virtual Private Networks (VPNs) to protect the integrity of transmitted data
- Specialized recommendations for network infrastructure and architecture design that optimizes the security and enhances the availability of your network
How Nextgen Firewall Works
Our team of certified security engineers will work closely with you to review your current network infrastructure, architecture, security goals and objectives so that we can validate your NextGen firewall / Unified Threat Management (UTM) security functions, configurations, and rule sets to ensure they are optimized to achieve your business requirements. We partner with your existing team to continually manage your NextGen firewall infrastructure, help troubleshoot and resolve issues, infuse best practices and tune your security infrastructure while seamlessly integrating with your change management process to implement approved requests, security patches and firmware updates required to properly secure your business. Your protection is further enhanced by our Security Operation Center (SOC) which provide 24/7 monitoring, alerting and reporting for your security infrastructure and escalates issues as needed.
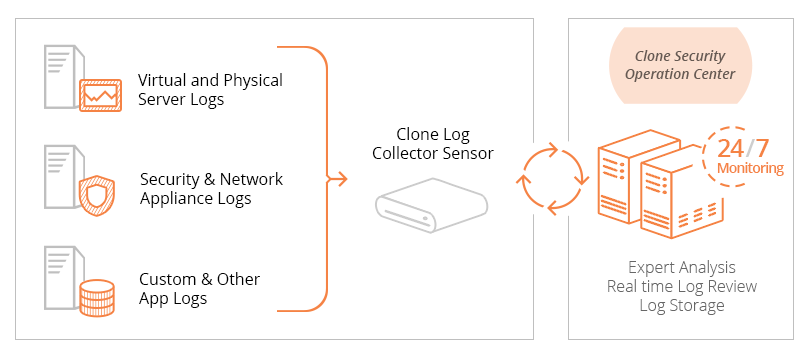
Log Management
Aggregate and quickly analyze your essential security logs
Allows you to quickly and easily review logs to find vulnerabilities and troubleshoot your network
- Log collection and storage with powerful parsing, classifying, and categorizing capabilities to allow you to easily identify vulnerabilities in your environment and capable of scaling as you grow
- Real-time search and analysis capabilities streamlining your ability to troubleshoot and perform postmortem analysis and forensic investigations
Empowers you with a holistic view of security events across your entire network, helps to quickly identify key areas that need urgent attention, and facilitates troubleshooting and resolution
- Monitoring and Alerting to identify traffic that requires further investigation with your team
- Security Operation Center monitoring your security environment, triaging and escalating alerts, and providing guidance where needed 24/7/365
With enhanced visibility and access to relevant log information you can expedite troubleshooting, remediation, compliance and audit requirements
- Maintain compliance with industry standards and regulations
- Detailed reporting of all security related logs for any device and endpoint on your network
Detailed reporting of all security related logs for any device and endpoint on your network
How Log Management Works
Our team of certified security engineers will work closely with you to review your current infrastructure and solutions and to identify the recommended devices that should forward logs so that you can maximize your ability to find vulnerabilities, identify suspicious activity, and troubleshoot your network. A Log Management device will be configured according to your business requirements so that your team can install it within your network and begin the process of forwarding essential logs that will be parsed, normalized, classified, and categorized into a central repository. We will then work closely with your team to train them on the intuitive Log Management solution so they can obtain a holistic view of security events across their network and quickly conduct real-time searching and analysis across a large volume of log information. Our Security Operation Center (SOC) will consistently monitor the logs sent to the Log Management device to triage events and escalate alerts as needed 24/7 so your team can expedite troubleshooting and resolution of urgent events that require your attention. Additionally, your logs will be securely archived on a nightly basis to Clone Systems enterprise data center to comply with industry standards and regulations and to support any future disaster recovery effort or forensic investigation.
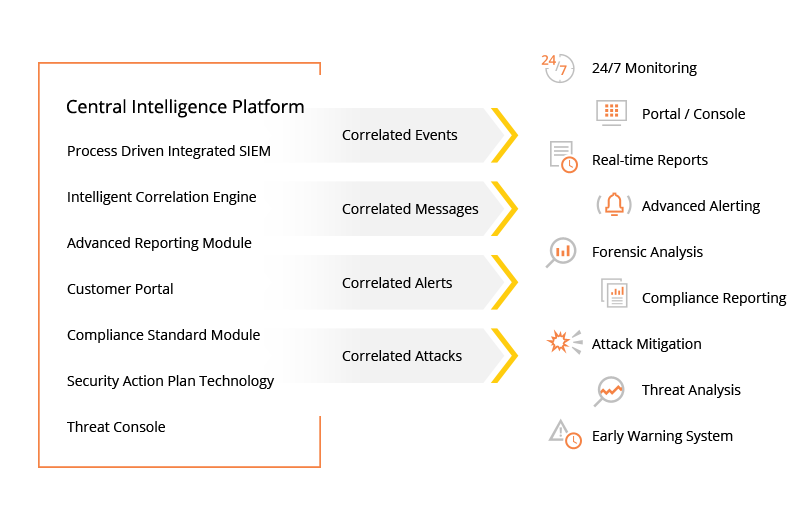
Security Information And Event Management (SIEM)
Conduct real-time analysis of threats by correlating log data from your network and security devices
Optimizes your security intelligence to help prioritize security team resources so they can focus on unique threat patterns that could negatively impact your security posture
- Correlating historical and real-time security information and events to identify patterns and trends to help prevent emerging threats before they occur
- Analyzing correlated events to investigate suspicious activity and determine the level of potential risk to the business
- Active threat intelligence consistently updated from multiple internal/external security sources
Maximizes your teams visibility of correlated events by providing additional insights and expertise that facilitates a deeper level of troubleshooting and resolution
- Monitoring and alerting to identify events that require additional investigation by your team in collaboration with our security experts
- Security Operation Center monitoring and analyzing your correlated events to identify and triage event patterns, and provide guidance and escalation 24/7/365
- Unified reporting of correlated security events occurring on your network
* SIEM Requires Log Management
How Security Information And Event Management (SIEM) Works
The Security Information and Event Management (SIEM) solution is built on top of the powerful parsing, normalization, classification and categorization capabilities provided by our Log Management solution. It actively inspects and correlates your historical and real time logs collected from your devices against consistently updated threat intelligence feeds, security signatures, and anomaly detection events to identify unique threat patterns and trends that could negatively impact your security. This correlated log data and any identified threat patterns are presented in our intuitive SIEM solution to facilitate a deeper level of troubleshooting and resolution. Our Security Operation Center (SOC) consistently monitors, analyzes and triages the correlated events 24/7 so that they can escalate prioritized alerts to your team as needed in order to help identify and prevent emerging threats before they occur.
Incident Response
Gain instant access to critical security expertise and technology to rapidly respond to and remediate a security incident and develop an incident response plan
Prepares your organization and Computer Security Incident Response Team (CSIRT) to respond quickly and effectively to a security incident when needed
- Retainer-based Incident Response resources to ensure the availability of security experts to work with your internal teams and respond to security incidents
- Proactive development of an Incident Response Plan that clearly details roles and responsibilities, procedures, communication plans and other key elements for addressing the most sophisticated of security threats
Reduces the cost of a security breach to your organization by promptly responding to a security incident and limiting the damage and recovery efforts
- A comprehensive suite of enterprise investigation tools and technologies used to quickly search your network for evidence of attacker activity
- An expert team of security engineers with extensive experience investigating breaches of all sizes and across many industries
Develop remediation plans that eliminate the security threats from your environment and identify security controls that reduce the likelihood of a re-compromise
- Evidence collected through forensically sound procedures and handled in a manner consistent with law enforcement standards
- Detailed investigative reports that analyze the security incident and address the needs of multiple audiences both internal and external to your organization
How Incident Response Works
Our expert team of security engineers will proactively work with your team to prepare a comprehensive Incident Response Plan or validate an existing plan so that your company is ready to promptly respond to cyber threats and minimize the impact of a security breach. Upon subscribing to our retainer service, we can quickly deploy critical security resources to work with your Computer Security Incident Response Team (CSIRT) to execute your Incident Response Plan and rapidly respond to a cyber threat or breach. Using forensically sound procedures we will determine the risks and identify a strategy for containing and stopping the attack. Once the immediate threat is mitigated we will leverage a suite of investigative tools and technologies to track down all traces of the threats and then work with your team to eradicate them and restore the impacted systems. After the remediation effort is completed a detailed investigative report will be delivered which analyzes the security incident and identifies any additional security controls required to reduce the likelihood of a re-compromise and to enhance the safety of your critical systems and data.

Professional Services
Gain instant access to critical security expertise and technology for ongoing assistance with improving your security posture and compliance
Assess the current security state of your business and solutions and identify and prioritize any gaps that need to be remediated to reduce risk
- Map your businesses security controls to the regulatory and compliance frameworks relevant to your industry to validate compliance and identify any risks that need to be addressed
- Focus on the interactions between users, apps and data to ensure security controls, process and policies are effective and resilient to common attack scenarios
- Evaluate your Disaster Recovery (DR) and Business Continuity (BC) plans and provide feedback aimed at helping you minimize business interruptions and manage through unforeseen disasters
- Develop a roadmap for evolving and maturing your security posture that can be reviewed with senior leadership to share progress and position justifications for additional resources
Review the security tools and technologies deployed in your organization and receive feedback on their effectiveness and guidance on additional solutions that can strengthen your defense against emerging cyber security threats
- Extensive vendor agnostic security knowledge with a deep understanding of the latest best practices used to help you navigate the array of security solutions and technologies in the marketplace so you can select the tools that provide the most benefit to your organization and reduce your business risk
- An expert team of security engineers with extensive experience defending against cyber security threats of all types and across many industries
- Robust networking knowledge versed in secure network architecture and topology design for small and large scale business networks spanning physical, virtual and cloud service environments
How Professional Services Works
Our team of certified security engineers are ready to partner with you to identify, plan and implement projects that improve and mature your security posture, strengthen your compliance, and reduce the risk that cyber security threats can have on your business. We compliment your existing security expertise by collaborating closely with your team to flush out any security gaps that exist within your processes, infrastructure and technology stack so that we can help you achieve your pressing security and business objectives.
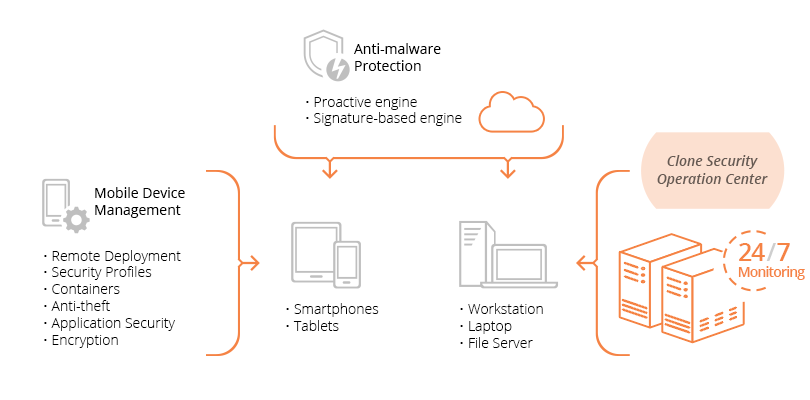
Advanced Endpoint Threat Protection
Protect your endpoints in real time and detect and prevent cyber threats
Facilitating immediate corrective action against suspicious endpoint activity threatening your environment
- Real-time threat detection, analysis, and response, which protects your endpoints against all types of malware
- Correlated threat intelligence providing a holistic view of known and unknown endpoint attacks
Provides additional security resources via managed solutions that free your team to focus on driving core business value
- 24/7 monitoring, alerting, and reporting of suspicious endpoint behavior across your enterprise
- Vendor agnostic expertise with best of breed endpoint solutions managed by certified security engineers
How Advanced Endpoint Threat Protection Works
Our team of certified security engineers will work closely with your team to deploy your best of breed Advanced Endpoint Threat Protection solution across all your Windows, Mac, Linux, iOS, Android, and other mobile device endpoints using an intuitive management console. The solution will protect the endpoints in real-time from malware security threats using the latest correlated threat intelligence and the Clone Systems Security Operations Center (SOC) will consistently monitors the solution and endpoint activity 24/7. If malware infects an endpoint, the Advanced Endpoint Threat Protection solution will alert on the suspicious activity so that the SOC can quickly contain and remediate the threat.
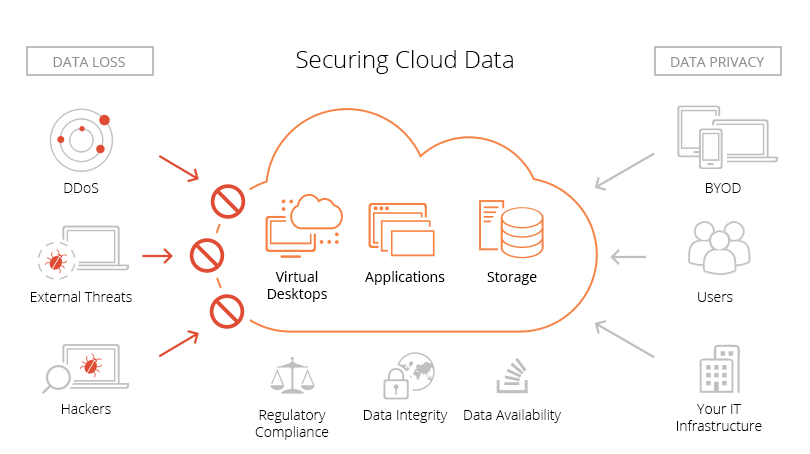
Secure Private Cloud
Rapidly scale your computing, security, and storage needs as your business evolves
Host your mission critical business applications and data in highly available industry compliant secure private clouds protected 24/7 by Clone Systems comprehensive suite of security services and solutions
- Securely store, transmit and process data while achieving the highest level of data security in accordance with industry standards such as Payment Card Industry Data Security Standard (PCI DSS), Gramm-Leach-Bliley Act (GLBA) / Federal Financial Institutions Examination Council (FFIEC), Health Insurance Portability and Accountability Act (HIPAA), Federal Information Security Management Act (FISMA), National Institute of Standards and Technology (NIST), North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Standard and Sarbanes-Oxley (SOX).
- Quickly scale and provision computing resources to adapt your secure private cloud to the evolving demands of your business
- User-friendly technical support provided by our Security Operation Centers and skilled and certified security engineers with extensive experience supporting a variety of operating systems and virtualization platforms
Minimize your business’s exposure to costly interruptions and unforeseen disasters by hosting your Disaster Recovery and Business Continuity Solutions in our secure private cloud
- Flexible cost-effective solutions that are tailored to your business requirements and optimized to meet your recovery objectives
- Maintain a common, supported desktop environment across your business while simplifying the process of deploying updates and changes
- Applications can execute in your compliant secure cloud and/or transparently communicate back to the resources hosted within your data center via a site-to-site VPN connection
Rapidly deliver virtualized desktops and publish applications to your organization via our Virtual Desktop Infrastructure (VDI) solution
How Secure Private Cloud Works
Clone Systems secure private cloud is highly available, delivered on proven and robust infrastructure, compliant with critical industry standards and regulations, and protected 24/7 by Clone Systems comprehensive suite of security services and solutions. We provide you with a simple interface for rapidly provisioning the virtual servers you need to address your business and technical requirements using your choice of a variety of operating systems and your custom application environment. Our team of certified security and network engineers are available to provide you with technical support and can assist with connecting your secure private cloud to your existing IT infrastructure using encrypted IPsec VPN connections so you can securely transmit and process data. As your computing requirements evolve you can quickly scale capacity and tailor your secure private cloud to the demands of your critical business applications.
Get Clone Guard Pricing and Product Information at:


